RS-Lynx risk filters
For analysts, posts on social media are the starting point for identifying threatening signals. We have created an extensive collection of risk filters that can be used immediately in your own monitoring projects. The set can also be used as an active monitoring unit thanks to the reverse function, i.e. filter becomes search topic. Our filters are multilingual in German, English, French, Spanish and Chinese.
Our risk filter package is not just a “passive” protection mechanism that automatically sorts out incoming hits – it can be used 1:1 as an active search in Talkwalker and other social media monitoring tools. This means that filter logic becomes a fully-fledged search profile that specifically detects risks instead of just cleaning them up afterwards.
What does that mean in concrete terms?
-
Passive (filtering): You first see “everything” – and then remove the unwanted.
-
Active (search profile): You define the risk grid as search logic and only receive the relevant risk signals as a hit stream from the outset.
The immense advantages
-
Early detection instead of post-processing: risks are proactively identified before they escalate – not just when they get lost in general monitoring.
-
Massively less noise: The search profile delivers high-quality hits with significantly fewer irrelevant mentions → faster sifting, higher precision.
-
Faster response, less effort: fewer false positives means fewer manual triages and shorter time-to-action.
-
Scalability & consistency: Once the filter logic has been defined, it becomes a standardized search template – consistent across teams, markets, languages and topics.
-
Better reporting and alert logic: If the hits are already “risk-clean”, alerts, dashboards and trends become much more meaningful (instead of being distorted by noise).
A sentence that sums it up
We transform filters from “Cleanup” to “Radar”: the same logic, but as an active search – for precise, proactive risk monitoring with maximum efficiency.
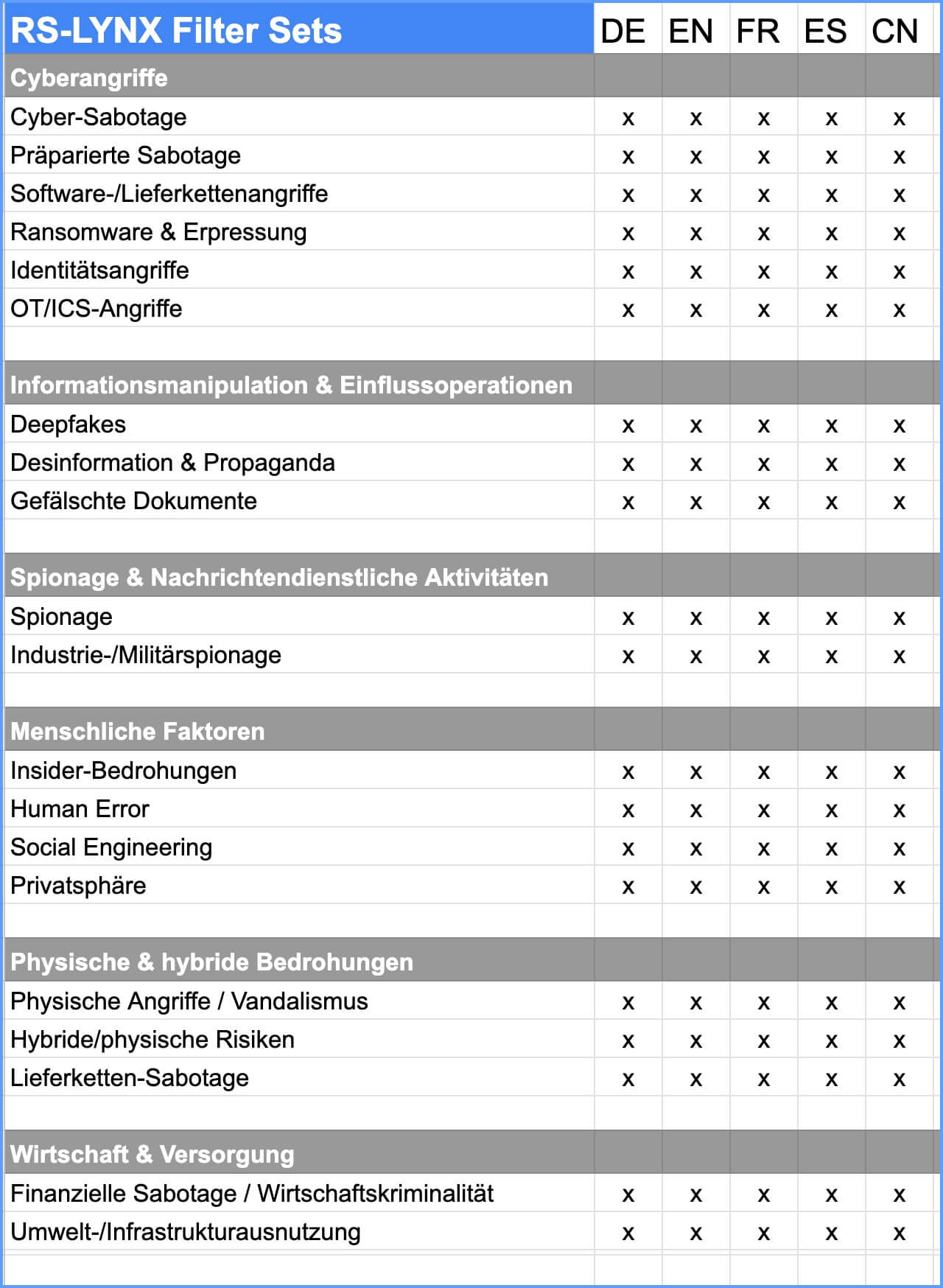
This filter package serves to identify complex threat situations in a structured, holistic and early manner – in digital as well as physical, organizational and strategic contexts. It covers technical cyber attacks, manipulative information operations, covert espionage activities, human risk factors including privacy-sensitive areas, physical and hybrid forms of attack and economic or supply-related threats. In this combination, the package enables a rapid classification of security-relevant events, improves the identification of attack patterns and supports a holistic risk and situation assessment.
1. cyber attacks
This group represents the most direct and effective forms of modern digital attacks. It includes technical compromises, system infiltrations, operational manipulations and attacks on industrial or digital supply chains. This makes it visible how systems can be infiltrated or put out of operation. This category is of particular interest to cybersecurity teams, incident responders, digital forensics, critical infrastructure operators and organizations with complex IT/OT landscapes, as it accurately depicts the technical patterns attackers use to infiltrate systems.
- Cyber sabotage
- Prepared sabotage
- Software/supply chain attacks
- Ransomware & blackmail
- Identity attacks
- OT/ICS attacks
2. information manipulation & influence operations
This category focuses on the targeted influencing of information, media, perception and identity. It includes methods used to manipulate content, distort realities or strategically influence social trends. The group is particularly relevant for OSINT analysts, investigative journalism, government agencies, platform moderation and reputation protection, as it represents common tools of modern influence campaigns, hybrid propaganda and digital deception that influence political decisions, business processes or public opinion.
- Deepfakes
- Disinformation & propaganda
- Forged documents
3. espionage & intelligence activities
This group describes covert, strategically planned information gathering operations – from industrial sectors to research and military areas. It encompasses typical patterns of long-term reconnaissance, technological leakage and targeted data exfiltration. It is of interest to security agencies, intelligence agencies, technology companies, research institutions and international organizations. The category helps to identify the operational signatures of organized actors, APT behavior and intelligence methods that often operate covertly.
- Espionage
- Industrial/military espionage
4. human factors
This group focuses on people as the central security component. It is crucial because over 70% of all successful attacks are the result of human error, manipulation or malicious behavior. It includes deception, misconduct, internal risks, manipulative behavior and the handling of sensitive personal data. It thus shows how people themselves – whether consciously or unconsciously – become a vector of attack. This category is interesting for HR, compliance, data protection, security awareness, internal audits and all organizations that work with confidential employee or customer data, as it depicts the main patterns of human vulnerabilities and data protection-related risks.
- Insider threats
- Human Error
- Social engineering
- Privacy
5. physical & hybrid threats
This group focuses on attacks that use physical intervention, on-site access or a combination of physical and digital methods. This includes situations in which physical manipulation makes a digital attack possible in the first place – or vice versa. This category is particularly important for operators of critical infrastructure, energy suppliers, logistics and transportation sectors, production facilities and security services. It shows scenarios in which digital risks turn into real damage and where attackers exploit several levels simultaneously.
- Physical attacks / vandalism
- Hybrid/physical risks
- Supply chain sabotage
6. economy & supply
This group looks at attacks and disruptions that affect economic systems, business processes, financial processes or operational supply. It shows how economic vulnerabilities can be exploited, financial flows manipulated or supply chains disrupted. This category is of particular interest to financial institutions, risk management, corporate governance, auditing and companies that are heavily dependent on global or critical supply systems.
- Financial sabotage / white-collar crime
- Environmental/infrastructure utilization
Status: 8.12.2025

